Windows 2003 Group Policies can do a lot of things; it’s such a big list of things that you can do in a Group policy, with the default templates, that it can be difficult to find a setting among the hundreds of fields and sub-fields in the Group Policy tool in Active Directory. There is an Excel spreadsheet called PolicySettings.xls that is searchable, and contains detailed explanations of each setting in the default Windows 2003 SP1 templates.
But there are a few key settings among all the registry keys that are critical to the success of a Citrix implementation.
•Delete Cached Roaming Profile – removes the roaming profile from the Terminal Server after the user logs off, and the changes have been successfully copied back to the central roaming profile directory. (used in conjunction with two others – “- do not detect slow connection” and “-wait for remote profile to load”) •Folder Redirection (to keep the size of the roaming profile down and keep the user’s data centralized and secure) •Lockdown of Internet Explorer / the Desktop (may require significant testing to make sure things aren’t too locked down to get the work done). •Loopback –replace /merge •Hide Drives on My Computer – determines exactly which drive letters a Citrix client can see, and has to take into account the home drive, the other network drives, and the remapped client drives. “Loopback-merge / Loopback-replace”
The “loopback merge” or “loopback replace” setting in group policy can be a critical component to getting the control over user access that a Citrix implementation requires:
First of all, the users don’t go in the users container, and the Citrix servers don’t go in the computers container, because they can’t be controlled with group policies; instead, separate containers, “OU’s”, are created by the AD administrator.
At the minimum, we require a single OU for the Citrix server we are implementing. As the Citrix integrator, we need to be able to control the type of access the users are getting when logged on to the Presentation Servers, and we use GPO’s, on an OU, to accomplish this.
As far as the users, they also don’t belong in a folder, but in an Organizational Unit. But there are a few different scenarios to look at with the users. If we are building the AD from scratch along with the Citrix implementation, we might as well create the “Citrix Users” OU; but we might more likely be bringing Citrix into an AD implementation that already exists, for completely different designs than “terminal services”, and the users already may have GPO’s controlling things like folder redirection and hiding server drives, in ways that conflict with what we need them to do.
In this case the Citrix integrator needs to be able to “lock-down” the Citrix SERVER Organizational Unit, so that already-existing users with conflicting user settings can come in without threatening the stability of the Citrix implementation.
In the case of the “folder redirection” GPO, we have to configure the GPO in the “user” section, since there is no corresponding setting in the “computer” section. But if we set a “user” GPO and put it on our one SERVER organizational unit, by default, we don’t get the guarantee that our GPO will work.
User settings will be read in AD first at the computer OU, but then at the user OU, and the user OU will win out if there are any conflicts, by default.
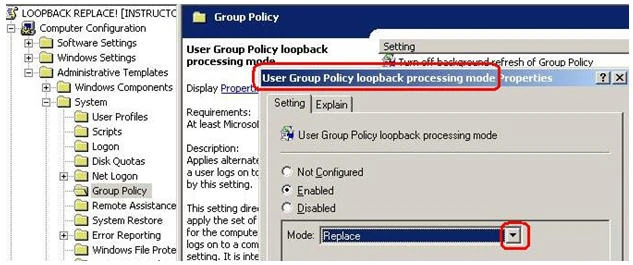
The key to controlling what happens is the “User Group Policy loopback processing mode” GPO setting. After setting it to “Enabled”, on the GPO of the OU of the Citrix server, the integrator has the option of setting it to either “merge” or “replace” mode.
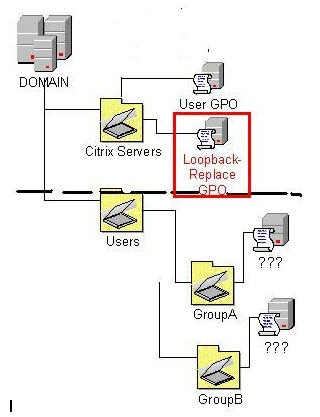
In the scenario where the integrator has no control over the GPO’s on the user’s OU’s, and the GPO’s could very well be conflicting, (in terms of which drive letters are hidden or revealed, for example, or how locked down a machine is), the integrator can use “loopback-replace”, to cancel out any user-settings that may have been assigned at the user OU, and then use another GPO to set all the user-settings that the users will have, when logging in to servers in that OU.
In this scenario, any setting under the “user” portion of the GPO will have to monolithic, meaning every user will have the same setting.
In another scenario, an organization can require differing types of access for different types of users. For instance, a regular branch employee may be restricted to only one mapped client drive that is going to correspond to their USB audio device files, and the other client drives are to be hidden, so that they cannot use the WAN for transferring data from their hard drives to the central “home” drive they are mapped to in the Citrix implementation; the manager at the branch, however, will be allowed to access his own client drives in the Citrix environment, and the transfer of files across the WAN will be at his discretion.
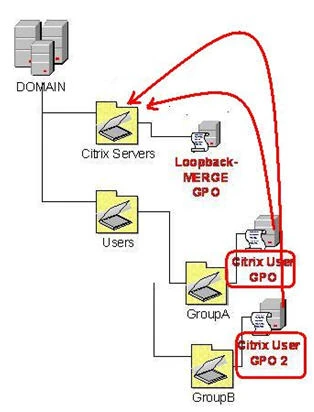
In order to implement this type of access, Citrix says the integrator needs to be able to control the GPO’s at the user’s OU’s, and designs different user GPO’s on those user containers.
With a different OU for each of the three types of users, the integrator can set up different user GPO’s, then, at the server container, the integrator places a “loopback-merge” GPO, in order to allow the various user rights to be “merged” into the Citrix Presentation Server’s environment, providing the user GPO’s of any user’s capable of logging in to these servers have been analyzed for any security or incompatibility issues.
A user is logging in to Terminal Services and getting this Terminal Services environment, often only after having logged in to a server or domain and run a different set of GPO’s for that environment. If the user is logging in from a Windows workstation, access that workstation itself is managed by AD as well; in the case of a thin client, there is less of a GPO management issue.
The Citrix integrator needs to provide access to mission critical applications. Some of these may be web apps, and may be provided by publishing IE on the Citrix Presentation Servers. This doesn’t necessitate the granting of access for users to browse the web through the Presentation Server, however. GPO’s can be set to restrict the users of the IE on servers in an OU to only a fixed set of websites. (These websites can be further enhanced with SSO by adding a Password Manager agent to the Citrix Servers.) As long as functionality of these websites is not impeded, the IE on the Citrix servers should be locked down as tightly as possible, and virus scan software installed, and internet traffic monitored, and filtered for only a fixed set of websites.
On the other hand, users may want or need access to external websites from time to time. This access can be assumed less mission critical, or it would be transferred to the Presentation Server environment. Therefore, the client machines should be less restricted, allowing web browsing, and less restricted access to the machine as well, compared to the Citrix environment of the same user account.
To accomplish this, the workstations reside in a different OU, separate from the Citrix servers. A loopback policy is placed on the workstation container as well, and in this scenario, the option would be “loopback-replace”. This way, the user settings that restrict drives, and IE and desktop access, and reside in GPO’s on the user containers, will be discarded, or “replaced”, when the users log in to the workstations, and there will be only minimal restrictions to replace them.
Then, within those varying user GPO’s, login scripts are pointed at to map home and shared drives, the settings to lockdown the server are set, folder redirection of My Documents and Desktop to the user’s home drive is configured, and “Hide Drives on My Computer” has to be configured, to control exactly what the user can see when connected to the Citrix servers.
The disadvantage of this design, though it is the Citrix and Microsoft “Best Practice”, is that it necessitates re-building the entire AD for the Terminal Services implementation, or building two different user accounts for each actual person - one for the terminal services and another for whatever the old AD account was used for.
As an alternative, there is a way to lock-down the Citrix server OU with “loopback-REPLACE”, while still configuring different types of user access. By adding the multiple, conflicting GPOs for different user types at the one server OU, with “loopback - replace” in place, we can go into “properties” on each user GPO, go into “advanced”, and highlight each group on the menu, de-select “apply group policy to”, then add a group from AD, like “managers”, and “apply group policy” only to that AD group.
The “apply group policy to” button is in the properties of the GPO, under “properties”, “Security”:
Hiding Server Drives
The TSC tool or a PSC policy can be used to enable or disable “client drive mapping”, and assuming the “remapping of server drives” has not been done, the client drives are going to be V, U, and T, possible continuing up the alphabet backward from there for any other existing client drives at the moment of connection.
The login scripts can get the user an “H” drive for home and an “S” drive for share. By default, the user gets access to the Presentation server’s drives, as they are in its own registry, most likely C, D, and E.
All this can be then filtered by a GPO that reveals, or not, each letter in the alphabet, if there is something there to reveal.
The problem is that in the standard Windows template file – the “system.adm” file on a standard domain controller, didn’t predict the complexity of this environment.
Among the string of V,U, an T, H & S, and C, D, and E, we want to reveal or hide various combinations. The interface in AD offers 6 different, pre-configured, variations in a drop down menu, on which drives to hide. The choices are “Restrict A&B”, “Restrict C only”, “Restrict D only”, “Restrict A B & C only”, “Restrict A B C & D only”, and “Restrict all Drives”.
The two more options we might be hoping for are “Restrict All but S & H”, and “Restrict S, H & T.
And there is a way to modify the ADM file on the domain controller(s) so that the extra options can be available. It involves typing the alphabet backwards into a calculator in binary, clicking 1’s for every letter to hide and 0’s for every letter to reveal, then converting the number to decimal, and appending the system.adm file on the domain controller. The MS KB article # 231289 details the steps;
One thing to watch out for is that the number of drive letters on each Presentation Server have to be standard and consistent, and this GPO is customized around that particular drive letter situation, as well as the client drive situation. Without standards in practice, the implementation will become a problem.
Since many people find themselves in the same situation with the need to hide specific drive letters other than the ones in the default windows policy template, there is a third party tool available from http://www.petri.co.il called gpdrivesoptions:
Source: Unitek Citrix Training Blog
EL MA$RY 08:10, 7 June 2009 (UTC)